Let’s face it, using Metamask is a lot easier than pulling out a hardware wallet, finding the USB cord, typing in the passcode, only to click through a bunch of hexadecimal values so you can finally hit “Approve”. And when we just want to mint the latest NFT or send a few tokens to a friend, going through the additional hardware wallet process can feel unnecessary. In some cases, it might be! Let’s get down to the bottom of the differences between software and hardware wallets.
What is a wallet?
To really understand what makes software wallets different than hardware wallets, we need to understand what a wallet really is.
There’s a common misconception that assets you own are stored “in your wallet.” It makes sense when we think about a real world physical wallet. You place your cash and coins inside a real, tangible thing. That is simply where the money is. However, that is not how a blockchain wallet works.
For any and all assets on the blockchain, the assets and balances themselves live… on the blockchain. The blockchain is a piece of data shared across all of the computers running that blockchain that holds a history of how much every address currently holds. It knows that Address A sent 10 ETH to Address B 100 days ago. It knows that Address C currently has 5 ETH and 2 Bored Ape NFTs. And it knows that Address D sent all of its funds to Address E yesterday.
Notice how we used the word “address” and not “wallet.” Because the blockchain really only cares about how much of each thing an address holds. That’s all it needs to know because your wallet doesn’t actually hold these assets. They’re simply associated with an address.
So what is a wallet? Well a wallet is actually a single piece of information: A private key.
This private key is a special piece of data that can be used to prove that a user is allowed to operate as a specific address. When a user “signs” something from a wallet which can happen when you send some tokens or mint an NFT or do anything else on the blockchain, what the user is actually doing is saying to the blockchain “Here is proof that I am the owner and operator of Address X and I would like to perform operation Z.”
So when we think about wallets, we should think of them as what we have control over, not what we actually hold. Which brings us to the important distinctions between software and hardware wallets.
Software vs. Hardware
The key distinction between software and hardware wallets is basically where you private key lives. Whoever has the private key, controls the assets in the associated address. And as a user of the blockchain, you want to make sure that no one ever gets access to your private keys!
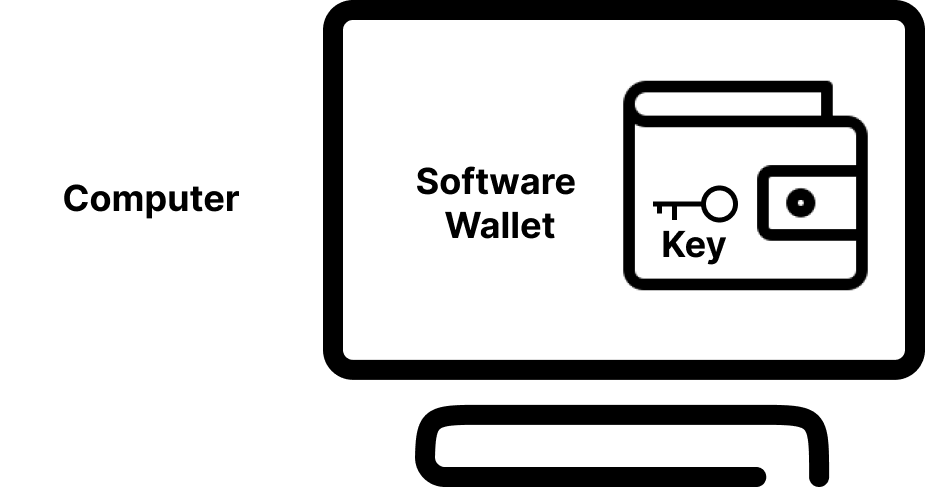
Software wallets keep your private key as a file on your computer. That file may be stored as part of a Chrome extension (like Metamask) or as a desktop application (like Exodus). What this software will do is ask you for a password that you choose and encrypt your private key using it. It stores the encrypted private key right there on your computer and when you type in your password you unlock the private key and make it usable for all your blockchain interactions. When you want to sign something, it loads in the operation you want to sign. It then uses the unlocked private key to sign it and send it off to be executed on-chain.
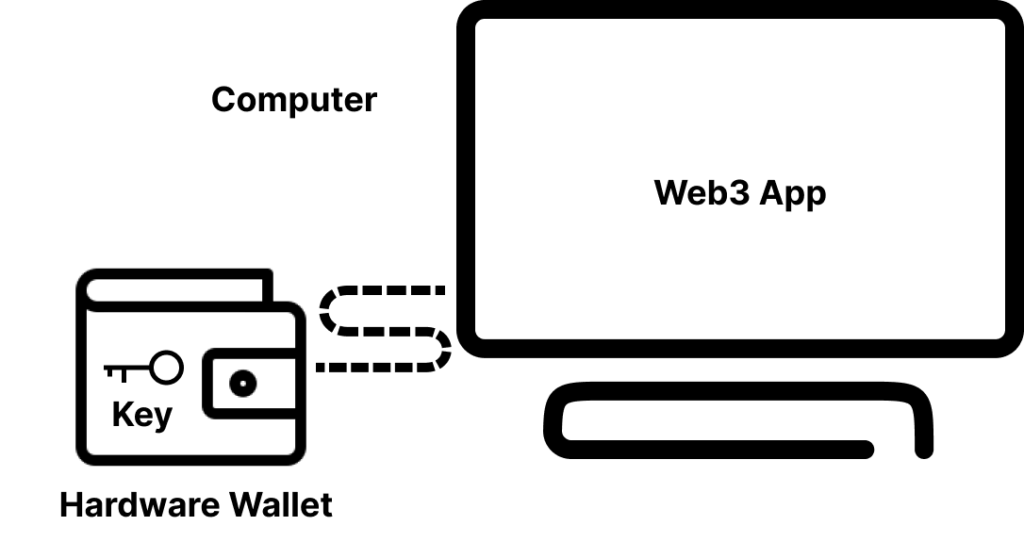
Hardware wallets keep your private key, you guessed it, on a separate piece of hardware. There are a lot of options for hardware wallets as well like Ledgers or Trezors, but they do require some up front investment in buying them. With a hardware wallet, your computer will decide what it wants to send off to the blockchain when you’re trying to send a transaction, but it will first send that information over to your hardware wallet. The hardware wallet will load up the private key, sign the message, and then send the signed message back to the computer to be sent off to execute on-chain. The private key, in the hardware wallet case, never touches your computer, only the finally signed message.
What makes a hardware wallet safer?
The most important value proposition of a hardware wallet is the fact that it never places your private keys inside of your computer. This guards your private keys against any quietly lurking malware that might be inspecting your computer’s files, looking for a private key that it can use to send assets to a bad actor. It also guards against your computer accidentally saving that private key somewhere in your file storage and losing it to someone who physically takes control of your computer.
Hardware wallets do not save you from making mistakes with malicious sites that pretend to do one thing, but really are out to take your tokens! You should read my previous blog post about a practical guide to safely minting NFTs to keep yourself safe in that case. But hardware wallets are a great tool for holding your most valuable assets in a place that you know can’t be accessed by anyone through software means.
Quick tips for hardware wallet usage
- Create different accounts inside your wallet for different purposes. If one is compromised through using a bad contract, at least it won’t affect all your tokens!
- Store your seed phrase in a completely separate place with good ol’ pen and paper. If you ever lose your hardware wallet by mistake, theft, or natural disaster, you can still recover everything on it if that seed phrase is safe elsewhere.
- Keep it up to date. There are sometimes updates that make it incompatible with the desktop apps. Updating it regularly will make sure you’re never stuck unable to get your assets out.
If you ever find yourself moving lots of assets from one wallet to another, check out Omnisender. It’s built to save you gas and time and make operating with those wallets much easier and safer. And if you’re looking to read more about blockchain, security, or Web3, check out more posts on the Omnisender blog!t